Information Security Management
Gemtek is committed to strengthening its information security practices to ensure that all information assets comply with the confidentiality, integrity, and availability standards defined by the ISO 27001 Information Security Management System (ISMS). These efforts are designed to reduce the risk of data loss, theft, leakage, tampering, misuse, or intentional damage, while also ensuring the continued operation of critical systems and business functions. At the same time, Gemtek ensures full compliance with relevant laws, regulations, and stakeholder expectations by implementing an Information Security Policy that requires all personnel to understand and follow in accordance with applicable procedures and guidelines.
Gemtek strictly upholds its contractual obligations and confidentiality commitments to clients. In compliance with ISO/IEC 27001, the Company has implemented the "Office Information Security Management Procedure" and the "Information Security Management Manual" to govern related operations. These measures aim to prevent unintentional violations of intellectual property rights and to safeguard the privacy and protection of personally identifiable information. The Taiwan headquarters serves as the Group’s Information Security Center, extending its information security policies and practices to Gemtek (Kunshan) and Gemtek Vietnam. All operations are managed in accordance with the principles of the ISO 27001 management system.
Information Security Policy
- All full-time employees, contract staff, and dispatched personnel engaged by the company are required to fully understand and comply with the information security policy and its related standards.
- All personnel have a responsibility and obligation to safeguard the information assets they access or use, protecting them from unauthorized access, alteration, destruction, or improper disclosure.
- Job assignments should reflect a clear separation of duties, with well-defined roles and responsibilities. Employees should be granted only the access and information necessary to perform their jobs, helping to prevent unauthorized changes or misuse of data and services.
- Employees are obligated to protect the company’s sensitive information and must not access, use, disclose, or share such information without authorization, especially with colleagues, vendors, or clients who are not directly involved.
- All personnel must install antivirus software on their personal computers and keep virus definitions up to date. The installation, use, or download of illegal or unauthorized software on company information assets is strictly forbidden.
- If an information security incident occurs, the responsible department must report it promptly in accordance with established incident response procedures.
- Business continuity procedures for information operations should be established. Critical systems must be equipped with appropriate backup or monitoring mechanisms, with regular testing and drills conducted to ensure uninterrupted business operations.
- Risk and security factors must be taken into consideration prior to the development of new systems or the deployment of IT infrastructure, to prevent potential threats to system security.
- Internal audit and risk assessment procedures for information security should be established. Regular audits and risk evaluations of information assets must be conducted to ensure compliance with security requirements and the ongoing effectiveness of the information security management system.
- Any actions that compromise information security and involve illegal conduct will result in disciplinary measures, and employees may also be held legally responsible.
Information Security Committee
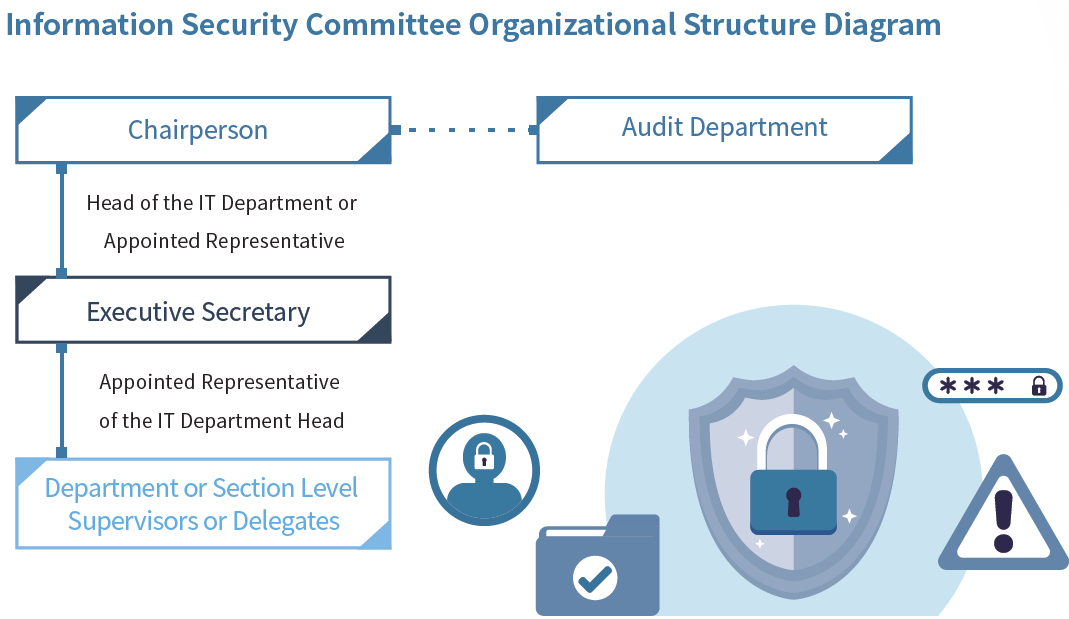
To further support its information security efforts, Gemtek established the Information Security Committee in 2010. The committee plays a key role in maintaining the effectiveness of the company’s information security management system and is responsible for driving and coordinating related initiatives. Chaired by the head of the IT department or a designated representative, the committee holds regular management review meetings to set and evaluate security goals and policies, ensuring that all information-related operations remain aligned with applicable laws and regulations.
In 2024, the committee held 2 review meetings, which addressed seven management review input items, including feedback on Information Security Management System (ISMS) implementation and internal audit results, as well as three output items, such as required documentation and records of review outcomes that must be retained by the organization. And completed the transition to the ISO 27001:2022 standard in August 2024, receiving third-party certification in the process. This system has greatly enhanced Gemtek’s ability to manage and enforce information security practices, helping to safeguard the assets of both the Company and its customers.
Information Security Protection Measures
To ensure the security of network communications, Gemtek has established the "Network and Communication Security Management Procedure" to continuously strengthen information protection and network operations management. A comprehensive email filtering platform has been implemented to block malicious threats such as viruses, spam, and phishing emails. In addition, a two-factor authentication mechanism has been introduced, requiring both a password and the employee’s mobile device to strengthen account protection and enhance overall security. Gemtek also promotes energy efficiency and carbon reduction by continuously consolidating servers and upgrading to high-performance virtual hosts and storage systems. To enhance network security, Gemtek has deployed internal firewalls and segmented its network to better protect server environments. The Company has also implemented a Managed Detection and Response (MDR) system along with incident response services, supported remotely by external cybersecurity experts. To prevent unauthorized access, VPN connections are secured with multi-factor authentication. Additionally, a Web Application Firewall (WAF) has been installed on the official website to effectively block DDoS attacks and reduce the risk of cyber intrusions.
Gemtek has also implemented a log analysis and traffic management system to conduct big data analysis of network logs, allowing for better visibility into network activity and the detection of unusual behavior patterns. Meanwhile, visitors who need internet access are required to complete either a “Visitor Internet Access Request Form” or a “Visitor Registration Form” in advance. Once approved, they will receive a temporary Wi-Fi account and password. Access is restricted to the designated guest wireless network, and connecting to the company’s internal network or any unauthorized network areas is not allowed.
Information Security Business Continuity Management
Gemtek has established a Business Continuity Management (BCM) process to reduce the risk of disruptions to its information systems. Within this framework, the company has defined specific recovery procedures and identified the necessary hardware, software, and support resources. The company also conducts regular Business Continuity Plan (BCP) drills, which include system and database backup and restoration, as well as service recovery exercises. The primary participants in these exercises are professional IT personnel. In 2024, Gemtek carried out a total of 59 disaster recovery exercises across various systems, simulating a range of impact scenarios. These drills play a key role in ensuring the continued operation of information systems and minimizing potential losses.
To assess the effectiveness of its information security controls and keep the Information Security Committee updated on the system’s status, Gemtek has defined 13 information security indicators, monitored on a monthly, quarterly, semi-annual, and annual basis. The Company also holds two internal management review meetings and undergoes one external audit each year to ensure the ongoing relevance, sufficiency, and effectiveness of its Information Security Management System (ISMS).
In 2024, all Gemtek sites successfully achieved their information security performance targets, and the external audit of the Taiwan headquarters found no major or minor deficiencies.
Information Security Awareness Training
To raise awareness of information security among employees, all Gemtek facilities regularly share briefings on recent cybersecurity incidents to highlight key risks and recommended precautions. Additionally, the company conducts training sessions covering topics such as security policies and network safety. In 2024, a total of 19 sessions were held, with 460 participants and a combined total of 634 training hours.
Personal Data Protection Policy
- All full-time employees, contract staff, and dispatched personnel engaged by the company are expected to fully understand and comply with this Personal Data Protection Policy and its related guidelines.
- Security Management of Personal Data Storage: Physical documents must be filed in individual folders and stored in designated locked cabinets. Access to electronic data is restricted through permission controls in accordance with information security policies.
- Job applicants, current employees, and former employees have the legal right to request deletion, access, review, supplementation, or correction of their personal data, and the company must not deny such requests.
- In the event of any infringement of rights, individuals may file a complaint or report the issue through the company′s designated email address or other official channels.
- If an investigation confirms a violation of this policy or any applicable privacy or data protection laws, the company will take disciplinary action against the responsible party. Legal action or claims for damages will be pursued when necessary, and all efforts will be made to minimize further harm.
Personal Data Protection Management
Gemtek is committed to the responsible use and protection of personal data and rights for both job applicants and employees. To support this commitment, the company has implemented a "Personal Data Protection Policy" in accordance with the Personal Data Protection Act and its Enforcement Rules. The policy applies to all personnel across the Gemtek Group, including those at the Taiwan headquarters, Gemtek (Kunshan), and Gemtek Vietnam, and covers full-time employees, contract staff, and temporary workers. If a suspected violation of personal data rights occurs, individuals can report the issue through the company's formal grievance channels.
All new employees at Gemtek are required to sign the "Consent Form for the Collection, Processing, International Transfer, Use, Protection, and Confidentiality of Personal Data" on their first day of onboarding. Both new hires and current employees must also complete the training on personal data protection as part of the company's integrity and ethical business practices program. In 2024, the completion rate for this training reached 100%.
Product Security
Gemtek considers maintaining robust information security during software operation a critical aspect of product responsibility, in addition to complying with labeling requirements and safety certification standards. The company has developed a comprehensive product and software design framework that includes hardware, firmware, and software. This framework is applied across the initial design, production, and end-of-life phases to safeguard against information leakage at all stages.
| Hardware Design | Software Design |
| Gemtek Technology specializes in telecommunications products. As such, market-specific concerns surrounding 5G networks are factored into the selection process for chip suppliers. The company designs hardware in accordance with end customers’ product security requirements and ensures compliance through relevant safety certifications. In addition, for certain products classified as central office equipment, Gemtek further evaluates protective measures related to installation and usage. These measures are supported by appropriate software-based detection and defense mechanisms to reduce the risk of physical intrusion. |
Our software is designed to enhance user data security through tailored products and services. In accordance with the principles of Zero Trust Architecture, we provide authentication features and secure access channels to support data encryption services.
|
| Firmware Design | |
| In selecting platforms, the company considers customer expectations concerning the security of software and firmware execution environments. Priority is given to platforms that support Secure Boot and Trusted Execution Environment (TEE) features. Additionally, all installed software and firmware must undergo digital signing and encryption to prevent unauthorized or uncertified code from being embedded into the platform. |



